With a wireless adapter in monitor mode you are able to sniff packet in the air:
at least the one in our range
even if we are not connected to that network
even if it’s not directed to our PC
To do this we need airodump-ng command, part of the aircrack-ng suite.
It a program design to capture packet with a wireless adapter in monitor mode
Ex:
root@kali:~# airodump-ng wlan0
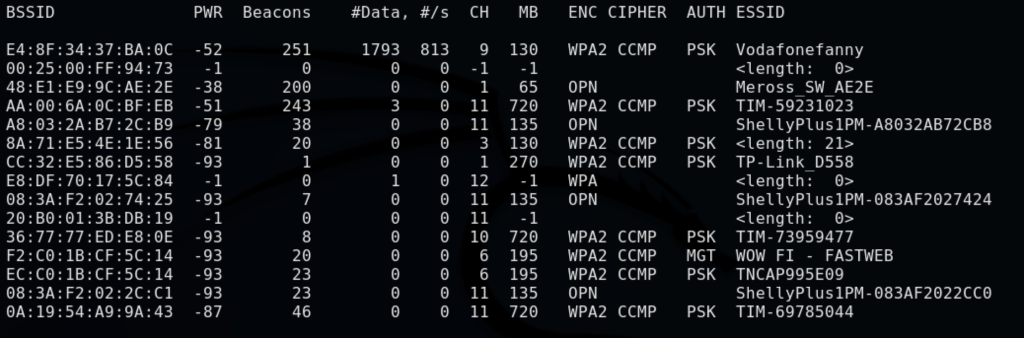
By default the airodum-ng shows only 2.4Ghz network frequency.
To get 5Ghz wireless frequency add –band a parameter, like this:
root@kali:~# airodump-ng --band a wlan0
Hte main bands are:
- a, 5Ghz
- b and g, 2.4Ghz
- n, 5Ghz an 2.4 Ghz
- ac lower than 6Ghz
It’s possible to use more than one basnds in the command line. The following command will show both 2.4Ghz and 5Ghz wireless:
root@kali:~# airodump-ng --band abg wlan0
Save sniffed data into a file:
root@kali:~# airodump-ng --bssid E4:8F:34:37:BA:0C --channel 2 --write test wlan0
In this case we write into the “test” file all packets sniffed from network whic mac address is E4:8F:34:37:BA:0C and channel 2.
the encrypted data sent to and from that target network are saved into the “cap” file

