Popular Python Libraries for Machine Learning
In the exciting world of Artificial Intelligence, having the right tools is crucial. In this lesson, we’ll explore three of the most popular Python libraries for machine learning: TensorFlow, PyTorch, and Keras.
TensorFlow
- What is TensorFlow? TensorFlow is an open-source machine learning library developed by Google Brain. It’s used for a wide range of machine learning and deep learning tasks, including neural networks, natural language processing, and image recognition.
- Tensorflow architecture is basically a multilayer APIs, where each top layer relies on the direct bottom layer
- Why is it Popular? TensorFlow is renowned for its flexibility and scalability. It’s highly preferred for building and training deep learning models.
- Who Uses It? Google, Uber, and Airbnb are just a few of the big names using TensorFlow for various AI applications. Learn more about TensorFlow.
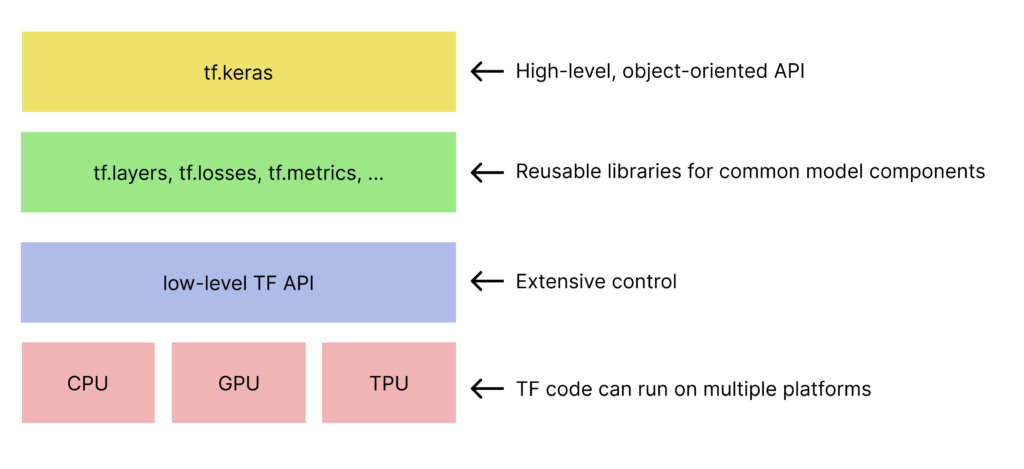
PyTorch
- What is PyTorch? PyTorch is an open-source machine learning library developed by Facebook’s AI Research lab (FAIR). It’s known for its dynamic computation graph, which is great for research and prototyping.
- Why is it Popular? Researchers and academics favor PyTorch for its user-friendly interface and dynamic computation capabilities.
- Who Uses It? Facebook, Twitter, and NVIDIA are among the organizations harnessing PyTorch’s power. Learn more about PyTorch.
Keras
- What is Keras? Keras is an open-source neural networks API written in Python. It serves as an interface for TensorFlow, Theano, and Microsoft Cognitive Toolkit (CNTK). Keras makes it simpler to build and experiment with deep learning models.
- Why is it Popular? Keras is renowned for its ease of use, making it an excellent choice for beginners. It also allows for seamless integration with TensorFlow.
- Who Uses It? Keras is widely used across various industries, thanks to its user-friendly approach. It’s a favorite for many startups and researchers. Learn more about Keras.
Choosing the Right Library
Selecting the best library depends on your specific project and goals. TensorFlow is great for large-scale applications, while PyTorch is fantastic for research and experimentation. Keras, with its simplicity and integration options, is often the choice for quick prototyping.
In summary, these libraries are the driving force behind many AI applications. Whether you’re diving into deep learning, conducting research, or building AI-powered products, having these tools in your arsenal will be a game-changer.
Quiz Time:
- What is TensorFlow primarily developed by?
- A) Facebook
- B) Google
- C) Microsoft
- D) Twitter
- Which library is renowned for its dynamic computation graph?
- A) TensorFlow
- B) Keras
- C) PyTorch
- D) Theano
- Which library serves as an interface for TensorFlow, Theano, and CNTK?
- A) TensorFlow
- B) Keras
- C) PyTorch
- D) Scikit-learn
- What makes Keras popular among beginners and for quick prototyping?
- A) Dynamic computation graph
- B) Ease of use
- C) Integration with PyTorch
- D) Complex syntax
Correct Answers:
- B) Google
- C) PyTorch
- B) Keras
- B) Ease of use