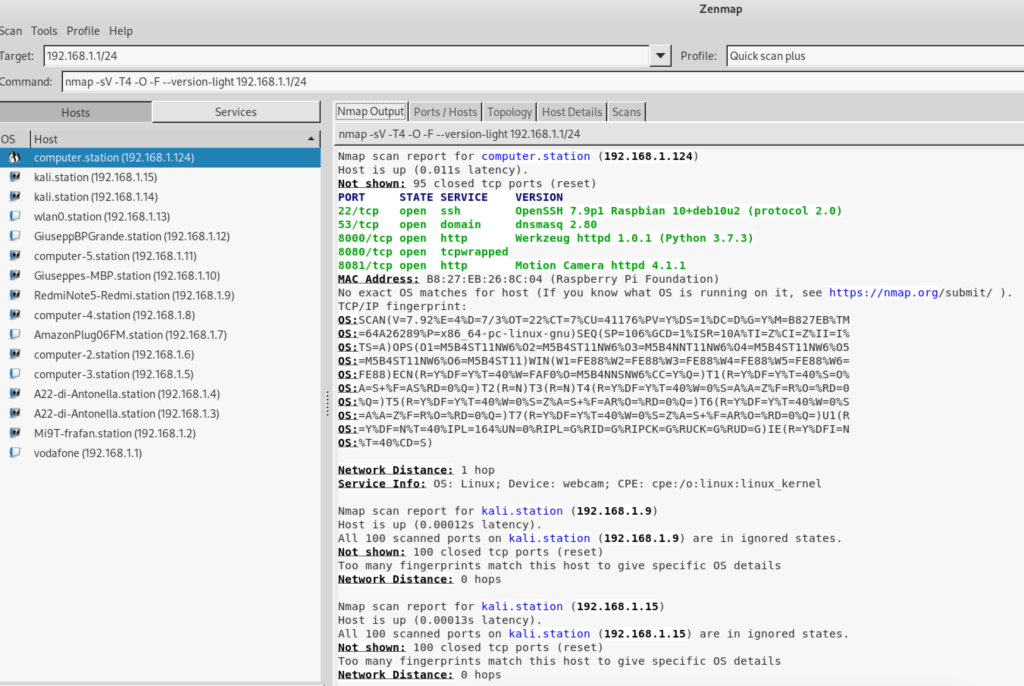
Metasploit Framework is a cybersecurity project that provides info about vulnerability, simplifies penetration tests and helps in the development of intrusions systems check.
It is an open source tool and basically executes exploits to a remote machine.
Let’s start
First of all we need to check if our Metasploit is correctly connected to Metasploit db. Type the following:
msfconsole
The result would be something like that:
root@kali:~# msfconsole
+-------------------------------------------------------+
| METASPLOIT by Rapid7 |
+---------------------------+---------------------------+
| __________________ | |
| ==c(______(o(______(_() | |""""""""""""|======[*** |
| )=\ | | EXPLOIT \ |
| // \\ | |_____________\_______ |
| // \\ | |==[msf >]============\ |
| // \\ | |______________________\ |
| // RECON \\ | \(@)(@)(@)(@)(@)(@)(@)/ |
| // \\ | ********************* |
+---------------------------+---------------------------+
| o O o | \'\/\/\/'/ |
| o O | )======( |
| o | .' LOOT '. |
| |^^^^^^^^^^^^^^|l___ | / _||__ \ |
| | PAYLOAD |""\___, | / (_||_ \ |
| |________________|__|)__| | | __||_) | |
| |(@)(@)"""**|(@)(@)**|(@) | " || " |
| = = = = = = = = = = = = | '--------------' |
+---------------------------+---------------------------+
=[ metasploit v6.2.18-dev ]
+ -- --=[ 2244 exploits - 1185 auxiliary - 398 post ]
+ -- --=[ 951 payloads - 45 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit tip: Adapter names can be used for IP params
set LHOST eth0
msf6 >
from Metasploit command line (msf6> in our case) it’s possible execute normally nmap
How to use Metasploit
We need toe execute 3 step:
find the service we need (ftp, ssh, …). Type:
search <serviceYouNeed> (let's say: search ftp)
After chosen your service, we search deeply the correct service to use:
info scanner/ftp/
Then, if we need to know which version of ftp my target is using, we should call the service using the “use” command:
use auxiliary/scanner/ftp/ftp_version
msf6 > use auxiliary/scanner/ftp/ftp_version
msf6 auxiliary(scanner/ftp/ftp_version) >
and so, to know the interface of the service, we type:
info (or: show option)
The result shows the list of the params of that service:
msf6 auxiliary(scanner/ftp/ftp_version) > info
Name: FTP Version Scanner
Module: auxiliary/scanner/ftp/ftp_version
License: Metasploit Framework License (BSD)
Rank: Normal
Provided by:
hdm <x@hdm.io>
Check supported:
No
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
FTPPASS mozilla@example.com no The password for the specified username
FTPUSER anonymous no The username to authenticate as
RHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit
RPORT 21 yes The target port (TCP)
THREADS 1 yes The number of concurrent threads (max one per host)
Description:
Detect FTP Version.
The required and not required aprams are show. Also the required ones, could have a default value so in tath case it’s not amdatory set that param.
To set a param we use “set” command:
msf6 auxiliary(scanner/ftp/ftp_version) > set RHOSTS 192.168.1.222
RHOSTS => 192.168.1.222
msf6 auxiliary(scanner/ftp/ftp_version) >
To execute the service type the “run” command (or the “exploit” command):
msf6 auxiliary(scanner/ftp/ftp_version) > run
and this is the result:
[+] 192.168.1.222:21 - FTP Banner: '220 ProFTPD Server (Debian) [::ffff:192.168.1.222]\x0d\x0a'
[*] 192.168.1.222:21 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf6 auxiliary(scanner/ftp/ftp_version) >
To recap, the (minimum) ordered list of the command to execute a service in Metasploit are:
- msfconsole
- search <serviceName>
- use <metasploitServiceName>
- info (or show option)
- set <param>
- run (or exploit)